 Some people ask me how they can “hijack” HTTPS API calls from an Android app. One of the best ways is to use PortSwiggers free Burp Suite, and hijack all traffic between your app and the server. One of the problems is, how do you add burp’s CA certificate to your android (emulator)? Burp’s help page simply says to look it up on google. Well, I hope this is one of the results showing up.
Some people ask me how they can “hijack” HTTPS API calls from an Android app. One of the best ways is to use PortSwiggers free Burp Suite, and hijack all traffic between your app and the server. One of the problems is, how do you add burp’s CA certificate to your android (emulator)? Burp’s help page simply says to look it up on google. Well, I hope this is one of the results showing up.
Note: This does not require any ADB pushes or so, and can be done in a few minutes. This was done under Ubuntu, using Android Emulator version 22.6.4. I’m uploading it into a Android 4.4.2 image running on a virtual Nexus 4.
Adding a CA certificate can be done in just a few steps, and will take a few minutes…
1.) Extract the CA Certificate from burp itself.
Set up Burp Suite, and set up a browser to use it as a proxy. Go to http://burp to find the page with CA certificate.
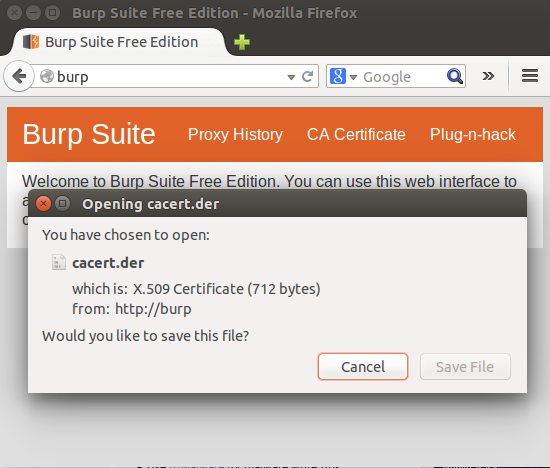
Download the certificate to your computer.
2.) Convert the certificate to the right format
The format you have now cannot be read by Android, so we need to convert it. This can be done using Brian Kelley’s RealmB website. Here you can upload your newly downloaded cert, and it will convert it:
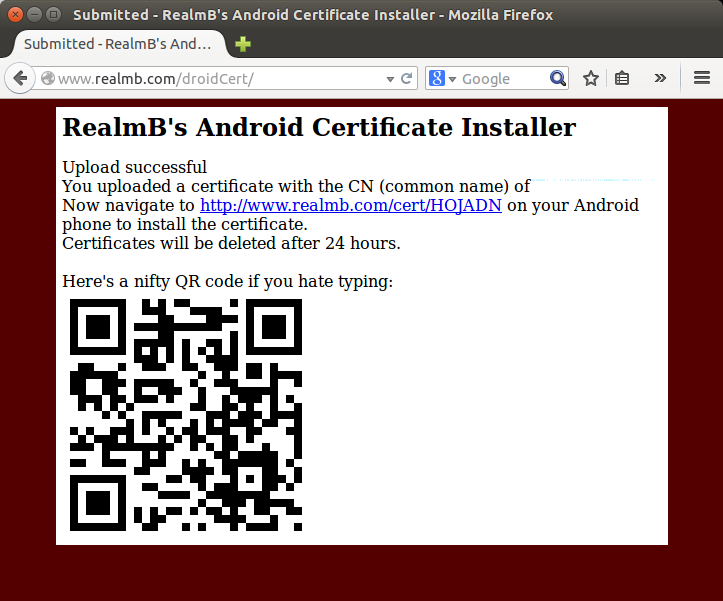
3.) Install the certificate
Brian’s website will give you a URL where you can download the new converted CA certificate. Surf to this URL from your Android emulator and click the link “Uploaded Certificate” to install it.
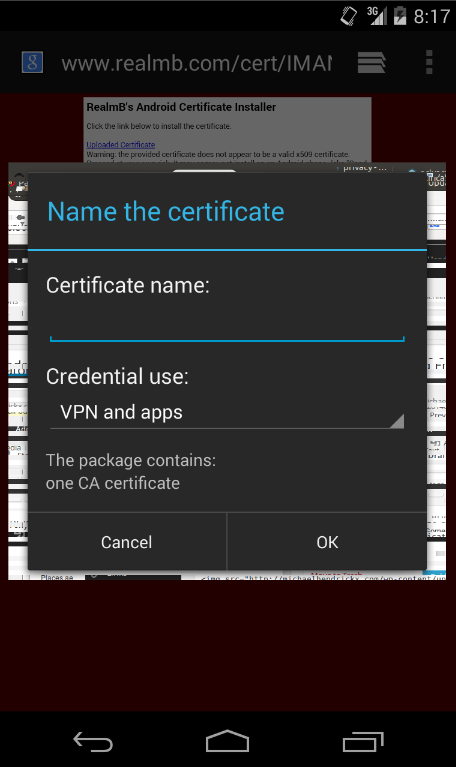
That’s it!
If you check Settings -> Security -> Trusted credentials, you’ll see under “User” that the new CA certificate is installed. On top of that, Android will warn you saying that “a third party is capable of monitoring your network activity”.
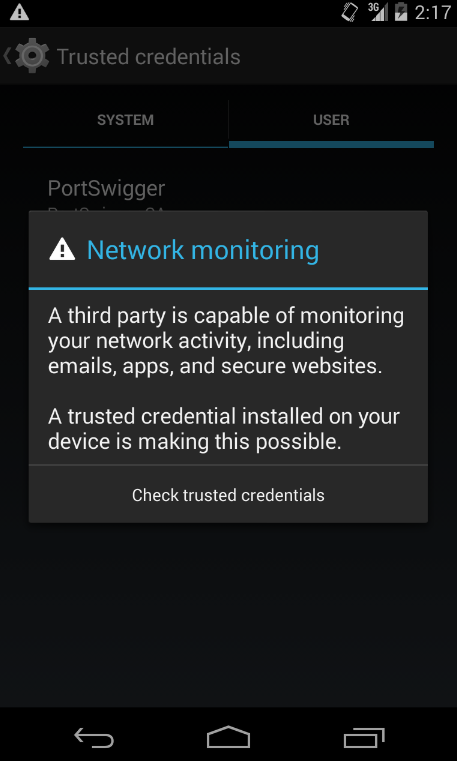
Alas, now when you start the emulater with a proxy set to the Burp proxy (make sure it’s listening several interfaces, not just 127.0.0.1):
$ ./emulator -avd ics-test -scale 0.60 -http-proxy 192.168.1.112:8080
You’ll be able to intercept HTTP and HTTPS data.
Leave a Reply